4 Advantages of a Key Management System in Facilities Maintenance
In this post
%20(1).avif)
1
2
3
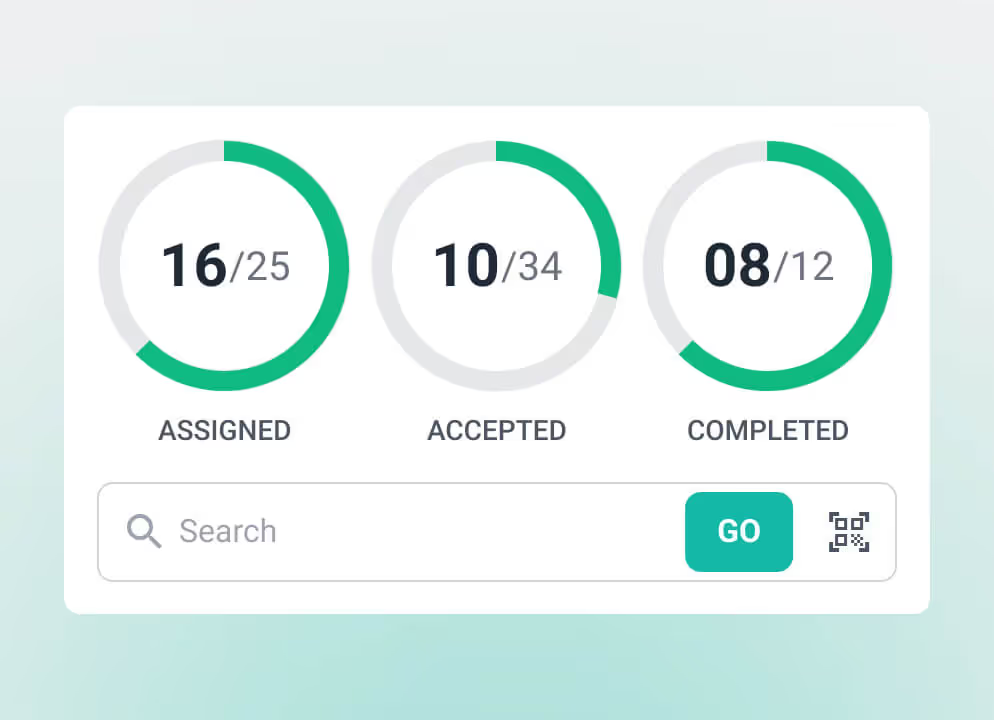
Deploying a key management solution can help you monitor, track, and manage the life cycles of all keys.
Have the following questions become part of the job for your maintenance staff?
If yes, your facilities personnel are not only wasting time on managing keys to various assets but also getting frustrated by it. While this may sound small, the effect it has on the overall maintenance operations. Especially, in this era of digital and improvised means of intrusion, theft, and whatnot. From preventing unauthorized access to a particular area or equipment to tracking the location of critical assets, the significance of keys has evolved over the years.
Inappropriate use of keys can wear out their encryption mechanism, increasing the chances of illicit usage. Why not consider securing the keys to various spaces and assets in your organization? Deploying a key management solution can help you monitor, track, and manage the life cycles of all keys. This capability is critical for asset-intensive enterprises as being aware of the usage of keys plays a major role in ensuring security and appropriate use of the assets.
With that in perspective, let’s take a look at 4 advantages of the WebTMA’s key management module:
Prevent unauthorized access to both keys and assets
Are you struggling to protect your assets from unauthorized users who aren’t eligible or legitimate to operate them? You are not alone. However, utilizing a key management tool can change the situation for the better. You can restrict the access of individuals to critical equipment and rooms by applying strict access control rules such as role-based access or the least privilege principle. This ensures that only authorized people have permission to access certain keys based on their job functions, departments, or designation. Besides, you can eliminate the manual juggling of keys with automated rules and workflows for key assignment. This ensures easy tracking of keys when contractors or third parties are involved. This way, both keys and assets are protected from unnecessary exposure and unauthorized usage.
Improve the life cycle of keys
In most organizations, keys are associated with valuable assets, equipment, or sensitive areas. Replacing them frequently can compromise their security and other functional performance. The integration of key management modules helps navigate this challenge by facilitating easy tracking of keys and their holders. This way, you will be aware of any tampering, damage, or biting done to keys. The module also integrates with physical security measures such as secure key cabinets. This provides a controlled and monitored environment for storing keys, which in turn, offers real-time insights into the status of keys – issuance, return, and replacement, among others. These measures ensure the keys are not just in good condition but also improve compliance adherence, operational efficiency with low-to-no downtime, and user satisfaction.
Get centralized view of all types of keys
One of the most challenging parts of key maintenance and management is keeping track of the master, sub-master, and departmental keys. This is where a key management tool comes into play, with its centralized database for users to monitor, track, and locate keys along with their associated key rings and holders. End-to-end key management helps you to:
Generate reports and drive decisions
Being aware of each key's history, usage, location, holders, and other essential information is imperative to determining key performance and asset maintenance, management, and security. The key management system helps achieve this by maintaining an audit trail of the details of every key, including:
All such information is critical for you to stay preventive and proactive about the access to, and the usage of, enterprise assets.
TMA Systems – a leader in providing all-round enterprise asset management solutions
TMA Systems has been in the industry for more than three decades, providing reliable, innovative, and trusted software for facilities maintenance. Our CMMS solutions have been helping organizations across industries to efficiently manage the maintenance and security of their facilities and assets. The key management module of our maintenance management solution – WebTMA – ensures the safety, security, and controlled use of every key within the enterprise premises.
Find out how WebTMA’s key management functionality can redefine the security and protection of your facilities and assets. Book a demo with our experts today!
- Protect your facilities and assets with clear visibility into who has key access at all times.
- Eliminate manual tracking headaches and reduce the risk of lost or misplaced keys.
- Streamline daily operations with faster key handoffs, automated logs, and simplified reporting.

Download the eBook now
You’re all set!
Your eBook is on its way to your inbox. We hope it brings fresh insights and practical takeaways to help you get more from your maintenance operations.
Explore related resources
.avif)
.svg)
Deploying a key management solution can help you monitor, track, and manage the life cycles of all keys.
Have the following questions become part of the job for your maintenance staff?
If yes, your facilities personnel are not only wasting time on managing keys to various assets but also getting frustrated by it. While this may sound small, the effect it has on the overall maintenance operations. Especially, in this era of digital and improvised means of intrusion, theft, and whatnot. From preventing unauthorized access to a particular area or equipment to tracking the location of critical assets, the significance of keys has evolved over the years.
Inappropriate use of keys can wear out their encryption mechanism, increasing the chances of illicit usage. Why not consider securing the keys to various spaces and assets in your organization? Deploying a key management solution can help you monitor, track, and manage the life cycles of all keys. This capability is critical for asset-intensive enterprises as being aware of the usage of keys plays a major role in ensuring security and appropriate use of the assets.
With that in perspective, let’s take a look at 4 advantages of the WebTMA’s key management module:
Prevent unauthorized access to both keys and assets
Are you struggling to protect your assets from unauthorized users who aren’t eligible or legitimate to operate them? You are not alone. However, utilizing a key management tool can change the situation for the better. You can restrict the access of individuals to critical equipment and rooms by applying strict access control rules such as role-based access or the least privilege principle. This ensures that only authorized people have permission to access certain keys based on their job functions, departments, or designation. Besides, you can eliminate the manual juggling of keys with automated rules and workflows for key assignment. This ensures easy tracking of keys when contractors or third parties are involved. This way, both keys and assets are protected from unnecessary exposure and unauthorized usage.
Improve the life cycle of keys
In most organizations, keys are associated with valuable assets, equipment, or sensitive areas. Replacing them frequently can compromise their security and other functional performance. The integration of key management modules helps navigate this challenge by facilitating easy tracking of keys and their holders. This way, you will be aware of any tampering, damage, or biting done to keys. The module also integrates with physical security measures such as secure key cabinets. This provides a controlled and monitored environment for storing keys, which in turn, offers real-time insights into the status of keys – issuance, return, and replacement, among others. These measures ensure the keys are not just in good condition but also improve compliance adherence, operational efficiency with low-to-no downtime, and user satisfaction.
Get centralized view of all types of keys
One of the most challenging parts of key maintenance and management is keeping track of the master, sub-master, and departmental keys. This is where a key management tool comes into play, with its centralized database for users to monitor, track, and locate keys along with their associated key rings and holders. End-to-end key management helps you to:
Generate reports and drive decisions
Being aware of each key's history, usage, location, holders, and other essential information is imperative to determining key performance and asset maintenance, management, and security. The key management system helps achieve this by maintaining an audit trail of the details of every key, including:
All such information is critical for you to stay preventive and proactive about the access to, and the usage of, enterprise assets.
TMA Systems – a leader in providing all-round enterprise asset management solutions
TMA Systems has been in the industry for more than three decades, providing reliable, innovative, and trusted software for facilities maintenance. Our CMMS solutions have been helping organizations across industries to efficiently manage the maintenance and security of their facilities and assets. The key management module of our maintenance management solution – WebTMA – ensures the safety, security, and controlled use of every key within the enterprise premises.
Find out how WebTMA’s key management functionality can redefine the security and protection of your facilities and assets. Book a demo with our experts today!
- Protect your facilities and assets with clear visibility into who has key access at all times.
- Eliminate manual tracking headaches and reduce the risk of lost or misplaced keys.
- Streamline daily operations with faster key handoffs, automated logs, and simplified reporting.

Register for your free webinar
You’re all set!
Your webinar is on its way to your inbox. We hope it brings fresh insights and practical takeaways to help you get more from your maintenance operations.
Explore related resources
.avif)
.svg)

Have the following questions become part of the job for your maintenance staff?
If yes, your facilities personnel are not only wasting time on managing keys to various assets but also getting frustrated by it. While this may sound small, the effect it has on the overall maintenance operations. Especially, in this era of digital and improvised means of intrusion, theft, and whatnot. From preventing unauthorized access to a particular area or equipment to tracking the location of critical assets, the significance of keys has evolved over the years.
Inappropriate use of keys can wear out their encryption mechanism, increasing the chances of illicit usage. Why not consider securing the keys to various spaces and assets in your organization? Deploying a key management solution can help you monitor, track, and manage the life cycles of all keys. This capability is critical for asset-intensive enterprises as being aware of the usage of keys plays a major role in ensuring security and appropriate use of the assets.
With that in perspective, let’s take a look at 4 advantages of the WebTMA’s key management module:
Prevent unauthorized access to both keys and assets
Are you struggling to protect your assets from unauthorized users who aren’t eligible or legitimate to operate them? You are not alone. However, utilizing a key management tool can change the situation for the better. You can restrict the access of individuals to critical equipment and rooms by applying strict access control rules such as role-based access or the least privilege principle. This ensures that only authorized people have permission to access certain keys based on their job functions, departments, or designation. Besides, you can eliminate the manual juggling of keys with automated rules and workflows for key assignment. This ensures easy tracking of keys when contractors or third parties are involved. This way, both keys and assets are protected from unnecessary exposure and unauthorized usage.
Improve the life cycle of keys
In most organizations, keys are associated with valuable assets, equipment, or sensitive areas. Replacing them frequently can compromise their security and other functional performance. The integration of key management modules helps navigate this challenge by facilitating easy tracking of keys and their holders. This way, you will be aware of any tampering, damage, or biting done to keys. The module also integrates with physical security measures such as secure key cabinets. This provides a controlled and monitored environment for storing keys, which in turn, offers real-time insights into the status of keys – issuance, return, and replacement, among others. These measures ensure the keys are not just in good condition but also improve compliance adherence, operational efficiency with low-to-no downtime, and user satisfaction.
Get centralized view of all types of keys
One of the most challenging parts of key maintenance and management is keeping track of the master, sub-master, and departmental keys. This is where a key management tool comes into play, with its centralized database for users to monitor, track, and locate keys along with their associated key rings and holders. End-to-end key management helps you to:
Generate reports and drive decisions
Being aware of each key's history, usage, location, holders, and other essential information is imperative to determining key performance and asset maintenance, management, and security. The key management system helps achieve this by maintaining an audit trail of the details of every key, including:
All such information is critical for you to stay preventive and proactive about the access to, and the usage of, enterprise assets.
TMA Systems – a leader in providing all-round enterprise asset management solutions
TMA Systems has been in the industry for more than three decades, providing reliable, innovative, and trusted software for facilities maintenance. Our CMMS solutions have been helping organizations across industries to efficiently manage the maintenance and security of their facilities and assets. The key management module of our maintenance management solution – WebTMA – ensures the safety, security, and controlled use of every key within the enterprise premises.
Find out how WebTMA’s key management functionality can redefine the security and protection of your facilities and assets. Book a demo with our experts today!


Related resources
Related resources
You’ve seen what’s possible—connect with us to learn how TMA Systems can support your goals beyond the event.
You’ve read the insights, now see how TMA Systems helps teams put them into practice.


From ideas to impact
You’ve read the insights, now see how TMA Systems helps teams put them into practice.


From screen to solution
You’ve watched what’s possible, now see how TMA Systems works for your organization.


From insight to implementation
You’ve explored the strategies, now see how we can bring them to life across your real facilities.


From insight to implementation
You’ve explored the strategies, now see how we can bring them to life across your real facilities.






.avif)